Almost everyone who has tried to penetrate the secrets of hacking, sooner or later met guessing, or if the attacks against the login forms, whose aim was to break the brute force (brute force) or dictionary attack (dictionary attack) user passwords. Over time, the testers also came out that it would be wrong to try using brute force or dictionary to estimate the location and names of various files and scripts stored on the server on which you do not keep any links. Meet you but could even cases where the application uses a unique ID for showing the user's profile or to address files. Series of numbers, however, may be leaky and seek that ID is occupied and which is free, would be to manually scroll through a truly superhuman task.
Oh, and just to all of the above activities (but not only them) are perfect just the module Intruder Burp Suite tools with which to learn about this part. Right at the beginning, however, worth mentioning that just Intruder in the free version of the Burp Suite significantly reduced and at cadence with which sends individual requirements. So if you need to use the full speed Intruder enough for you to send hundreds request per second, you have to look for paid professional version.
Intruder use for guessing
Vertical or horizontal guessing, or send different passwords for one user name, password, or testing one for all users, it is the basic practical skills of many a novice attacker. However, we will not acquainted with guessing because we like the bad guys penetrated into foreign accounts, but because guessing is currently one of the basic techniques used during penetration testing. In the following paragraphs, therefore, we look at the different types of attacks, testing the strength of user passwords by using tools Burp Suite.
We harvest usernames
If you do not test the presence of weak passwords only one user whose login is known to us (eg. Admin), is a good idea to first prepare a list of logins that are registered in the application. Possibility to pull out of the application dictionary attack or brute force usernames is quite often a defect in logic of Web applications. As an example of vulnerability, for example, will bring out the registration form, which we dutifully announce whether the name is free or occupied. Similarly, the act also forms intended to receive a new password to us in the event that you wish to send a password to login existent, tells us that the specified name was not found in the database. Let us prior to use Guessing Intruder first to harvest usernames.
As always, we will not try anything on foreign Web application, but rather to try everything on our already well-known sandbox, which for us becomes our webmail Hack. If we go to the registration page of the new user account and try to register an account with login "admin" gets us answers "entered login is already used". This site will therefore ideal for harvesting logins.
So, run by our old friend Burp Suite and set your Web browser so that all requests flowed through him. There is no point stopping Intercept requirements and therefore this option to disable the Proxy module. Then send the completed registration form, and we'll look into the history of communication, whether our request properly recorded. Find request directed to the address /user/send_registration.php, and the now familiar procedure via the context menu sends it to the Intruder (Sent toIntruder).

Among the tabs at the top of the Burp Suite tools we find the labeled Intruder a single click on it to move to yet unknown destination. Do not despair, however. After reading this article, you will feel at home here.
Under the major tabs of each module similarly as repeater located in ear tabs labeled 1x, 2x, 3x, etc. depending on how many requests you to Intruder sent. Use these bookmarks between different requirements can switch or the cross behind the figures may conclude it is no longer needed.
Further below you will find a tab named Target, Position, and Options payloads for us today will be very important.
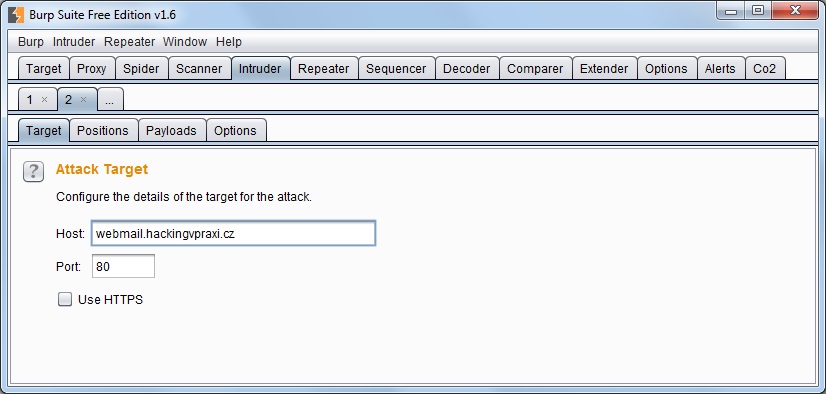
- Target - Target Attack card has more or less intuitive meaning. It contains the address of our destination, port, and possibility of using the HTTPS protocol. If we do not change our goal, I see no reason to alter anything here. If you have this card after all the changes made, be sure to make the same adjustments also in HTTP headers tabPositions.
- Positions - Position tab Payload he expects us to determine the type of attack and select locations in the request, which will be referred Intruder enter the required values. Intruder in our request to the Positions tab will automatically choose the appropriate injection site values. This place wrapped signs of Section § color and we are accentuated. Cause we'll want to choose yourself variable whose value we will test, click on the right side, click Clear§. Subsequently, the mice mark the value of the variable login (in our case "admin") and click the Add button §.Thus, we chose a place to which we intruder will automatically insert the name of the dictionary, which will determine whether a particular login in the application is authorized or not.
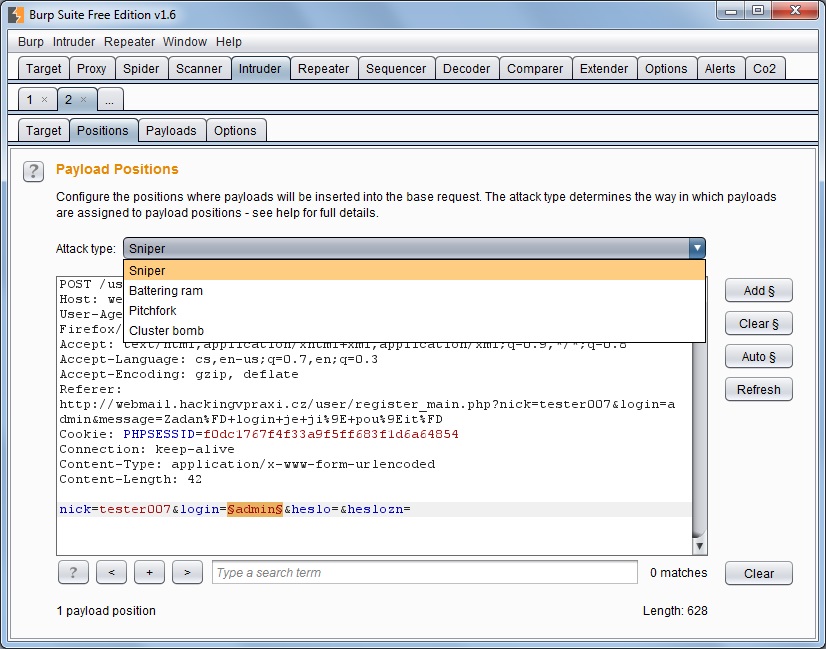
On the Position must not forget also choose the type of attack (Attack type). We have:- Sniper - This type of attack is expected that in the HTTP request mark only one point, which will Intruder insert specific values. At each request is therefore tested only a single parameter value. In practice, this type of attack is used, for example, when trying different passwords for a particular login, or as in our case, we test whether a particular login in the database already exists.
- Battering ram - Like type Snipper here with each request changing only one payload. Unlike the aforementioned but it can be inserted at multiple sites in the same request. This means that if the code mark two places with signs § will be on both these places when you send Request inserted Intruder same value. In practice, this type can be useful, for example, where the request includes changing the value in multiple places at the same time, or when testing if users do not use the same password to login.
- Pitchfork - During the test, it is possible to select more than one HTTP request (to 8) venues that are inserted payload from various sources. If we had identified two sites (eg. Name and password) and then select two dictionaries (one with names and second password) will be sent during the test requirements are always the first record of the two dictionaries, then second, etc. Example: Login1: password1, Login2: Password2, login3: password3, loginx: heslox.
- Cluster bombs - Even in this type of attack can be identified in the Request to 8 places for inserting the payload. Unlike the type Pitchfork but here they test all possible combinations. Usage is precisely example, when searching for the right combination of username and password. Example: Login1: password1, Login2: password1, login3: password1, Login1: Password2, Login2: Password2, login3: Password2, Login1: password3, Login2: password3, login3: password3.
- Payloads - If we are on the previous card duly marked place values on which we want Intruder input the required payload, and we chose the appropriate type of attack, it is now time to determine what values will be chosen places actually files. These settings can be found on the card payloads.
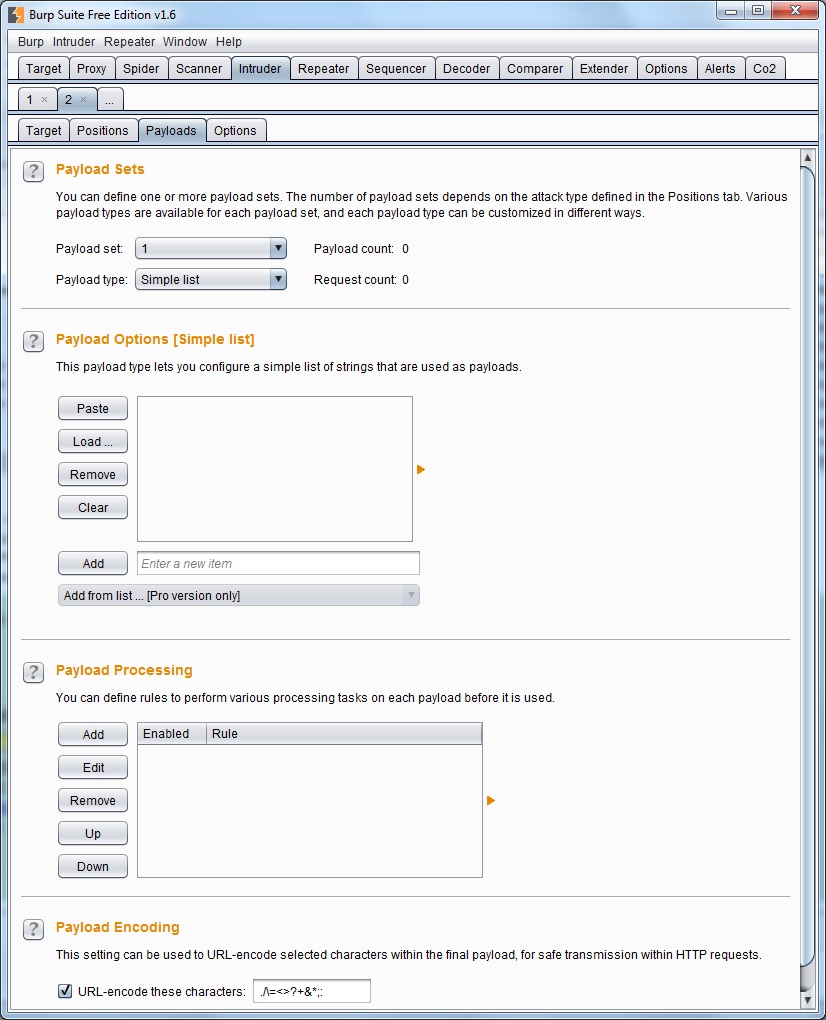
In the event that we are on the previous tab labeled more seats for inserting the payload (which is related also elected Attack Pitchfork, or cluster bomb), then we drop down below Payload field set to choose from so many options, how many sites are marked on request. Every time you select from the dropdown list one of the values (1, 2, 3, ...), this means that sets the payload, which will be put on a position corresponding to its position in the request.Example: If you would like to request tagged two points username and password (in this order in the request), then we payloads on the card in the list set Payload selected first gear and set out what payload will be put on instead of login. Consequently, we chose from a list of two and set the type of payload password. If it is still not entirely clear, everything I will show later in the embedded video. If we have chosen the appropriate entry from the list Payload set (in our case for the harvesting of user logins to the type of attack Snipper we only have one), we can move on to the next pull-down Payload type list, from which you select the type of payload. Again, we have a wide range of options.- Options payloads [xxxxx] - the contents of this section varies depending on the type of payload follows:
- Simple list - if we choose this type of payload is up to us to fulfill the required chain table that we want to test. Manually so we can build a simple vocabulary. This option is likely to use at times when we will try to test only a few string values. 5 For example, the most commonly used passwords.
- Runtime file> - Allows you to test inputs from a dictionary stored in a text file. Each record has yet to be placed on a separate line.
- Custom iterator - A very handy tool that lets you build vocabulary strings exactly to the liking of the tester. Let's say that we have registration numbers of employees in the shape AA25-3AV, AA04-6ER,AA88-3AB, etc. Choosing Custom iterator allows us to stack the vocabulary of strings that match this shape. By selecting Position, select the character position in the string and the list below to put all the characters that this position can be found. Thus, we can fill up to 8 different positions. For each position can also follow separator that define the field Separator for position x. In our case, we introduced the first position AA (note that it may be used Multi-character combination, and therefore does not always go just about individual characters), the second, third and fourth position we put the digits 0-9, with the third, position followed by a separator minus. On the fifth or sixth position, we then put uppercase alphabet AZ.
- Character substitution - Individual characters strings, which we can populate the list, using the substitution can be converted to other characters. Befitting it may, for example, in cases where we know that the goal is often used instead of the character and fours, instead of the character E troika and instead of the character O zero.
- Case modification - This option allows for individual entries from the list, change the size of letters used.
- Recursive grep - This option allows you to obtain the following payload is always the answer to the previous question. Regular expressions used to extract the contents of the response are defined underOptions section Grep - exract.
- Illegal Unicode - This type paylodu can be used to generate unauthorized representation of Unicode characters.
- Character blocks - This option allows you to test applications on the input strings of different lengths.Select a character or string, from which the resulting block compose, enter start and end the string length and size of the increase in length each time you send.
- Numbers - A very useful feature allowing, for example through the records by their unique id. Select the desired range and step numeral system, whether they be a whole or decimal numbers, or other advanced options, and we can start testing.
- Dates - If the input data is expected, once again we have the opportunity to choose the start and end dates, pace, and format.
- Brute forcer - If we have no choice but to try to break brute force, offering us Intruder own bruteforcer. Just define the desired characteristics and minimum / maximum length of chains tested.
- Null payloads - This type of payload use if we need to send a few requests with an empty value. How many sending occurs depends on the value that we make available on a single input field.
- Character frobber - gradually goes through each character of the input string and dropped it in the ASCII table on one level. Useful for example when we need to determine which part of the value of the input string has an impact on application response, and the changes which parts of her behavior evident.If you keep the option chosen Base value of payload position will test performed with labeled chain of the original request, or you can string field Specific define their own test string. Example: If the original string value "admin" will alternately perform tests on strings bdmin, aemin, adnin, admjn, ADMI.
- Bit flipper - this option allows the chain to flip selected bits for each character.
- Username generator - Add to the list the user name, such as "Full name", or in the form of e-mail addresses will be tested in all sorts of variants curtail and jointing names. Example: After entering the name "Roman Kümmel" will be tested as a combination of a RKummel, r.kummel, romances, novels,apd.
- ECB block shuffler - This option allows you to shuffle blocks of cipher text using the ECB.
- Extension-generated - Allows the user to connect to an external Burp Suite generator of accessories, which must be correctly registered Burp Suite.
- Copy other payload - If we request more marked locations for testing, they can use the same payload.Of course it would be easier to use Battering ram type attack, but imagine a case where in one place you need to upload files, for example login in plain text, while at another place the same login encrypted using base64. Now in this case we use this option when the field Copy from position will list the order of the payload requirement, whose value we want to take and in the Payload processing to add it to require encryption.
- Payload processing - After selecting the desired type of payload here you have yet another additional options for modifying the payload before using it. The individual strands can, for example, add a prefix or postfix, we can determine whether or not to encrypt the string before using or zahešovat, reverse the order of characters in a string, apd.
- Encoding Payload - last section available on the card determines the payloads for which the characters to be used in requests a URL coding.
- Options payloads [xxxxx] - the contents of this section varies depending on the type of payload follows:
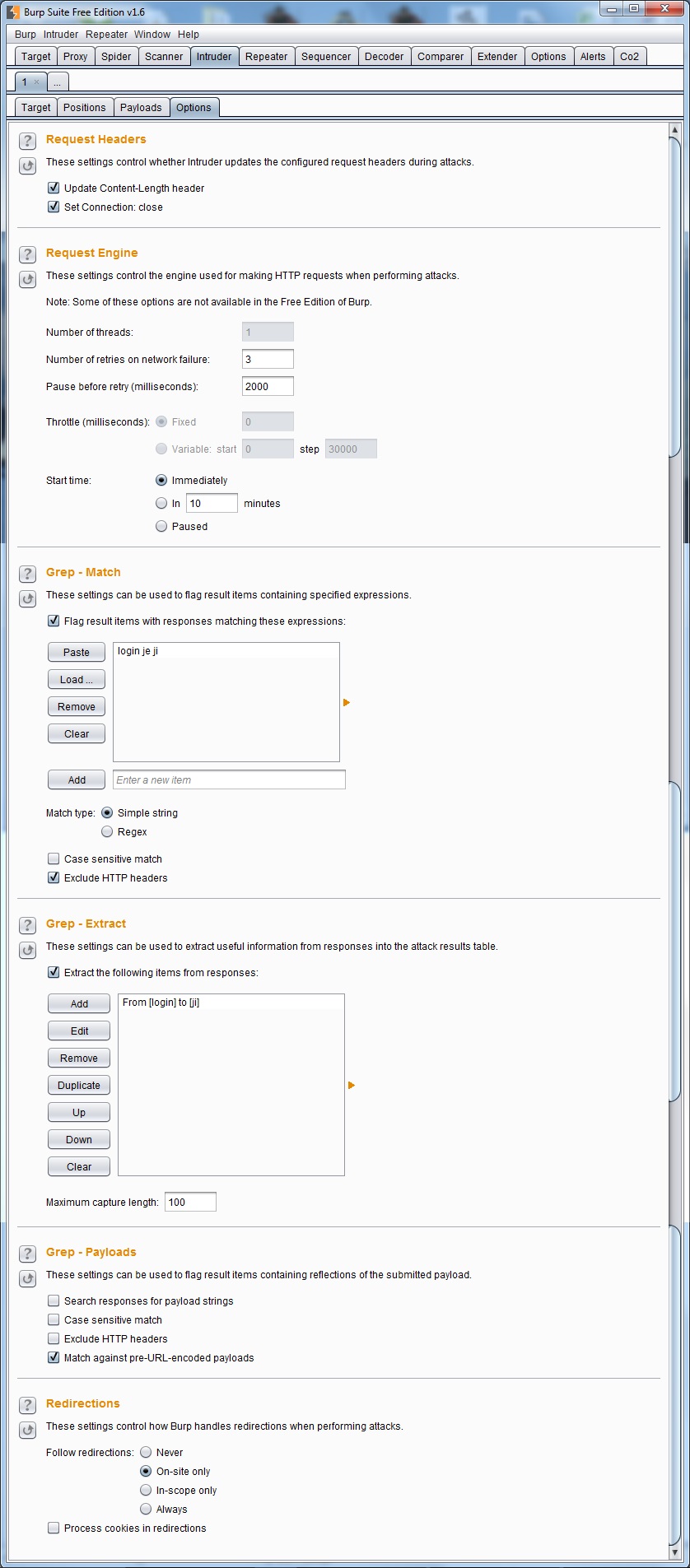 Options - At the moment, therefore, we have chosen instead of an HTTP request, which we insert payload, and we have chosen the appropriate type of payload. For our purposes, we chose Runtime file and selected a disk file with a dictionary of frequently used logins. Now we are left only to learn Intruder automatically detect whether the username is busy or available, which we will now further Optionstab.
Options - At the moment, therefore, we have chosen instead of an HTTP request, which we insert payload, and we have chosen the appropriate type of payload. For our purposes, we chose Runtime file and selected a disk file with a dictionary of frequently used logins. Now we are left only to learn Intruder automatically detect whether the username is busy or available, which we will now further Optionstab.- Request Headers - In this section we have two choices, which should be left checked
- Update Content-Length header - ensuring conversion of the value of the body length in the HTTP request header, payload if there is a change to change its size.
- Set Connection: close - Informs server that behind each answer immediately closed the connection.
- Request Engine - very important section in which we can influence the speed of the entire Intruder. As I wrote at the very beginning of this text it is precisely Intruder in the free version of the Burp Suite at these options very limited. In the event that we had available the Professional version, we should at this point able to set:
- Number of threads - the number of concurrent threads that can work Intruder stepped up considerably.
- Number of retries on network failure - the number of errors in a row, which may occur in connection pending the completion of the test.
- Pause before retry (milliseconds) - You can set the length of time between attempts in case the connection fails.
- Throttle (milliseconds) - Regulating the speed requirements. Here you can set the time interval between each request, which can be either fixed or can be linearly increasing with each request. Speed Adaptation is useful in cases where our test could cause a DoS, or in cases where the protective mechanisms applications allow users to upload to the server only a certain number of requests at a particular time.
- Start time - test we can run immediately or at this point we can schedule a delayed start.
- Attack Results - In this section, we set some other options Intruder behavior during the attack.
- Store requests - all outgoing requests will be stored in a temporary file, so you will be able if necessary to view the full text.
- Store responses - Like the previous option, this also serves to store room unit during the test.Specifically, this option allows you to store all server response.
- Make unmodified baseline Request - This option after Intruder requires that prior to the test reset all indicators payload and the first requirement in a row # 0 Posted empty values payload, which will provide the basic response of the server against which it will be possible to compare the following Request.
- Use denial-of-service mode - Check this option to switch to the mode Intruder susceptibility testing server against DoS at the application layer. Intruder will send requests, exactly as we have already described, but will not wait for an answer. Instead, after sending each request immediately terminates the TCP connection, and immediately sends another request.
- Store full payloads - Checking this option is necessary if we want the attack to perform certain actions, such as changing settings grep or change the content payload. This option, however, consumes more memory.
- Grep - Match - As we show later after running attack can be individual server responses flagged whether they meet the conditions specified by us, or not. And this section is the place where these conditions can be defined.If we want to use the identification of individual responses, allow her choice Flag result matching items with responses proposition expressions.
The table then place depending on the option you have selected under the table Simple string / Regex either specific strings, whose presence in the responses we verify or regular expressions.- Case sensitive match - determines whether a string comparison plays a role insensitive.
- Exclude HTTP headers - off the search string in HTTP server responses. If we expect that the change in server behavior depending on the input will be reflected in some of these headers must uncheck this option.
- Grep - Extract - This very useful tool allows you to extract from the website any data that varies depending on the submitted payload. As an example application that takes as a parameter the user id and in response to this request displays a Web page that contains the user name corresponding to the id. Harvest user names will be in this case a breeze, and because it's a nice example of the use Intruder, so this procedure later show.
If you require extracting certain data from the website simply in this section, tick the Extract seuraavilla items from responses and click the Add button. Appears us another offer, in which we set static text, that is, before the desired place to extract (start after extraction) and static text that is behind him (at Enddelimiter). Can be selected but also the position of the first character string in the response (at Start offset)and the fixed length of the extracted string (End at fixed length), or a combination of these. The second variant, as can be required data in response target is to use regular expressions.
The explanation we have two choices left undescribed election and one button:- Exclude HTTP headers - tick this option to drop the HTTP headers searched. Therefore, if data is to be extracted is located in these headers, the choice uncheck.
- Update config based on selection bellow - a simple tool to facilitate configuration of the extraction rules. If you have this option checked, just in the area that displays the server RESPONSE mark required for extraction and string instrument we have automatically fills in all required fields.
- Refretch response - Pressing this button we can try again to retrieve the code page, to verify that the required space correctly labeled.
- Grep - payloads - This area is determined by the testing reflected in the response payload display server.
- Search for responses payload string - Turns search payload in response to the server. It may be useful for example when testing the application on reflected XSS. If we have a list of strings payload testing the XSS, this way we can test whether our projected directly input and output. Activating this option adds a new column test results with information about the (un) successful search.
- Case sensitive match - Set the case must match the payload and the response.
- Exclude HTTP headers - Excludes the search area HTTP response headers.
- Match against pre-URL-encoded payloads - If you are sending some characters encoded with URL encoding, is likely to be on the server side decoded and displayed directly. To be encoded string of payload found in decoded form in the reply, this option must be checked.
- Redirections - Last section determines how it will behave Intruder when the server returns a status to redirect to another URL.
- Follow redirections - We can thus specify whether redirects to follow or not, and if so, whether such anywhere, or only within the same domain or domains within which we put into the scope.
- Proccess cookies in redirection - important choice that will affect whether at of redirect will also send cookies that we, together with a request to divert received. This option needs to be considered, we test the login form.
- Request Headers - In this section we have two choices, which should be left checked
After that, we have successfully set all the required values, now is the right time to launch the test. To do this, we used the Start option attack available by clicking Intruder in the main menu above the tabs card modules.
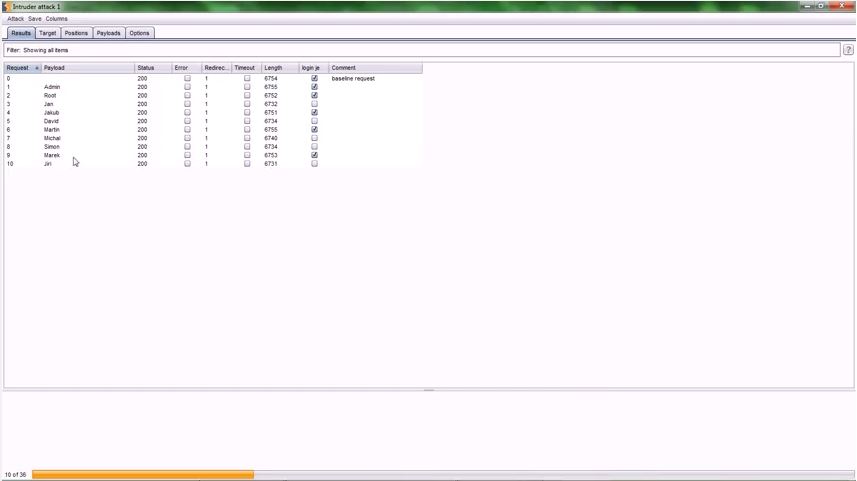
If we have everything set up correctly, if we free version only receive notice of the fact that the Intruder in the free version is limited and then you can watch the new window the progress of the test.
Video showing the steps for harvest usernames
Harvest user names based on the user id
As I promised in the paragraph devoted Grep - Extract is using Intruder very easy to extract the content of user names based on their id (of course suffer if this type of Web application vulnerability logical). One known targets for this extraction as CMS Wordpress, which in this respect is sufficiently chatty.
Using Google dorks, it is possible to find several million Word Press, which we list our users quite happy to offer:
And now to the actual procedure, which I will describe in writing, but only via the video below.
We test password strength
At this point you should be able to independently test the password strength of individual users in our test webmail, which we are using the procedure described previously dug out an application. For sure it will only recall different variants of attacks that can be used for testing passwords.
Dictionary Attack (dictionary attack)
 This type of attack to crack passwords trying to find the password in a dictionary (a file with a specific string). So if users use as your password, common words or names, their discovery using appropriate vocabulary relatively simple matter. On our site you can find some dictionaries in thedownload section.
This type of attack to crack passwords trying to find the password in a dictionary (a file with a specific string). So if users use as your password, common words or names, their discovery using appropriate vocabulary relatively simple matter. On our site you can find some dictionaries in thedownload section.Brute Force Attack (brute force attack)
 Brute force attack is used at times when the password is a common word and dictionary methods to fail. However, if a user password is set too short, or know the characters of which a password is made, we can try to break it by this method that tries to use every possible combination of selected characters. In the case of a large keyspace is the use of this method is so time-consuming that password cracking is not feasible in a reasonable time.
Brute force attack is used at times when the password is a common word and dictionary methods to fail. However, if a user password is set too short, or know the characters of which a password is made, we can try to break it by this method that tries to use every possible combination of selected characters. In the case of a large keyspace is the use of this method is so time-consuming that password cracking is not feasible in a reasonable time.Horizontal Attack
Horizontal attack means that we will test one password (or a few passwords) to all users. Let's say that one of the most common passwords in the Czech Republic, the word "password". Thus, let's try to use this password for all of us identified user accounts.
Vertical Attack
For vertical attack, we will try to break the password of a particular user (or a few users). It can be used in both dictionary attacks or brute force attack.
Complete Attack
By combining the horizontal and vertical variation of the attack we get when we will test all possible passwords for all user accounts application. This type of attack is very time-consuming.
All types of attacks you should be able to experience the Intruder Burp Suite of tools to handle themselves. For sure, but I attach one more video that captures some of the procedures.
www.youtube.com/embed/A1qMeU8-cBw
Conclusion
I believe that you are convinced of the fact that the module Intruder is a very useful tool which can test anything you can possibly think of. Mining logins and password crackers were just a small example of the wide spekra possibilities Intruder provides testers. The next time you test how applications handle if it receives a specific input, try to remember this tool and save you a lot of time that you would otherwise spent manually testing.
Post a Comment